I used voltage glitching to dump the code of the Tamagotchi Friends.
Recently, I experimented with the EEPROM of the Tamagotchi Friends. I didn’t manage to get code execution, but it was evident that segments of the EEPROM were copied into RAM, which could be used as a shell code buffer if need be. James Slater suggested using glitching to jump into this buffer, similar to how a Gameboy ROM was dumped.
In the past, I’ve been skeptical of using glitching to dump the Tamagotchi ROM, as it doesn’t have any evident security mechanisms or instructions that would be useful to bypass, but the suggestion made sense. The original vulnerability I used to dump the TamaTown Tama-Go had very long odds of working, but ended up working because 6502 is so forgiving with regard to exploitation (in that it doesn’t have an MMU, and always continues executing in the face of invalid opcodes and memory addresses). I figured that if I could move the program counter at all through glitching, even randomly, there was a good chance that it would eventually execute any code I had placed in RAM.
I started by putting some code that would write to the LCD plus a NOP sled into the EEPROM, and cycled the power.

Set-up. The wires to the Arduino are used to write the EEPROM and glitch the power. The drill bit is to push the buttons
I started by turning the power on and off repeatedly, but the Tamagotchi reacted very forcefully to this, shaking hard enough to fall off the table due to the noisemaker vibrating. I eventually changed the code to turn the power on and off only a few times. After a few tweaks, it was executing the code in the EEPROM about 10% of the time!
The video below shows the code execution, if you look very closely, one segment (four pixel) of the LCD near the top left becomes all black due to the code executing.
Playing with the code a bit, it turned out I could execute roughly 50 bytes total of code in two pieces of RAM I could jump between. With some help from Mr. Blinky, I wrote code that would dump the ROM via SPI through the buttons of the device (port A). It was pretty slow going, in 50 bytes there wasn’t room to initialize everything, so the code depended on some values already being set correctly, so was quite unreliable. But it did work, and I was able to slowly dump the ROM.
Looking at the ROM, it was very similar to the TamaTown Tama-Go ROM. Some of the ROM pages are in different places though. Pages 0 through 3 were code pages and page 4 was all code ‘stubs’, which is two fewer code pages than the Tama-Go. Pages 5-9 were blank, and pages 10-18 were images. The image pointer table was in page 14. Pages 19-21 contain mysterious data which could be compressed audio, or could be the Tamagotchi’s soul. It’s hard to tell. Pages 22 on were all 0xFF (disclaimer: I didn’t actually dump after the first few).
Some cute highlights of the image pages are below.
Awww …
Next up is to analyze the ROM!


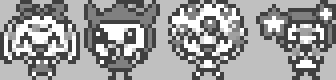

14 responses to Tamagotchi Friends Code Dump